Stop opening new files or installing apps on your Windows PC without trying them out in Windows Sandbox first. This built-in mini-Windows is totally isolated from your main installation, so if you aren’t already using it for testing, you should start today.
What is Windows Sandbox?
The Windows Sandbox is a feature that provides users with a completely isolated Windows environment to test in. It’s been available since Windows 10 19H1 to users with a Windows 10 or 11 Pro, Enterprise, or Education license. Unfortunately, Windows 10 and 11 Home users can’t use the feature.
It looks a lot like a virtual machine, but it’s a little bit different. For starters, this isn’t your typical VM. It’s self-destructing, meaning that when you exit the sandbox, it completely resets. Any files you’ve opened, any changes you’ve made, and any apps you’ve installed are removed, making it the perfect test environment.
Windows Sandbox will warn users that any data within it will be wiped when the app is closed.
If you’re running Windows 11 22H2 (or later) you can restart from within the environment without it self-destructing. This is a feature Microsoft added to allow you to use apps in the sandbox that require a restart to complete their installation. The environment is still temporary and, should you exit the sandbox app, it’ll reset to the default configuration.
It’s isolated from your main system, so even if you end up with a malware infection in the sandbox, it won’t impact your main Windows installation. By default, access to the internet is enabled via your network adapter, but this can be stopped by using a sandbox configuration file.
What Should You Use the Windows Sandbox For?
Windows Sandbox isn’t a feature that Microsoft really pushes on users, but as far as I’m concerned, it’s an essential weapon in the security and privacy toolkit.
Let’s look at the basics. First, most users will receive a malware infection because of something that they themselves do. They might open up a virus disguised in a suspicious PDF file, or install a cracked version of an app that’s riddled with malware.
You might be lucky. You might find that those infections are picked up by Microsoft Defender (or your own third-party antivirus). In sandbox mode, however, it doesn’t matter. The infection can’t damage anything. If you see a problem, you can just close the sandbox app. The infection is wiped without impacting anything in your main Windows installation.
I use the sandbox mode for any new app I install where I might question its origins or safety. I’ve also used it in the past to open up file attachments, especially with more troublesome file extensions.
You’ll Need the Right System (And Windows License)
While Windows Sandbox is intended to be a more lightweight version of Windows, it’ll still have an impact on your system performance, which means you’ll need a good enough PC to use it. Microsoft’s minimum requirements for a PC capable of running Windows Sandbox include:
- 4GB of RAM, while recommending 8GB or more. I’d recommend more, too, especially if you’re looking for a smooth experience.
- 1GB of free disk space to run, preferably on a solid-state drive (SSD).
- A 64-bit CPU with at least two cores and with virtualization support, but a 4-core CPU with hyperthreading support (or better) is recommended. If you’re running Windows 11 22H2 or later, you can also run Windows Sandbox on ARM64 CPUs.
There’s also the licensing to consider. As I mentioned, you can’t use the sandbox mode in Windows 10 or Windows 11 Home. You’ll need to upgrade your license to either Pro, Enterprise, or Education editions of Windows 10 or 11, or consider a more traditional virtual machine environment as an alternative instead.
How to Enable the Sandbox on Your Windows PC
If you haven’t used the sandbox before, you’ll need to set up a few things first. To start with, make sure that you’ve enabled virtualization for your CPU in your BIOS or UEFI menu.
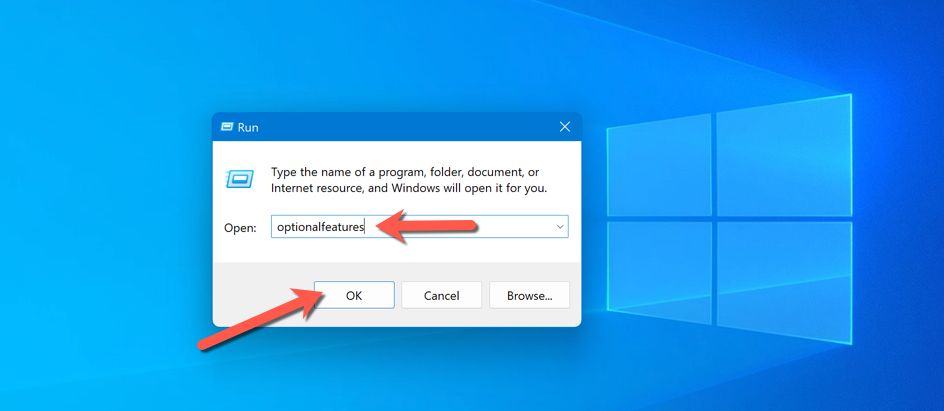
You’ll also need to install the files required for Windows Sandbox in the Optional Features menu on Windows 11 or on Windows 10. To do this quickly, press the Windows+R, type “optionalfeatures”, and press “OK”.
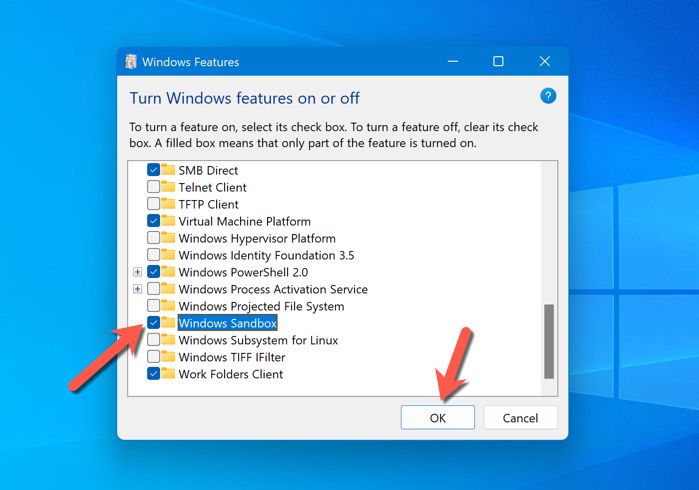
In the window that opens, make sure to select “Windows Sandbox” before pressing “OK” to begin the installation.
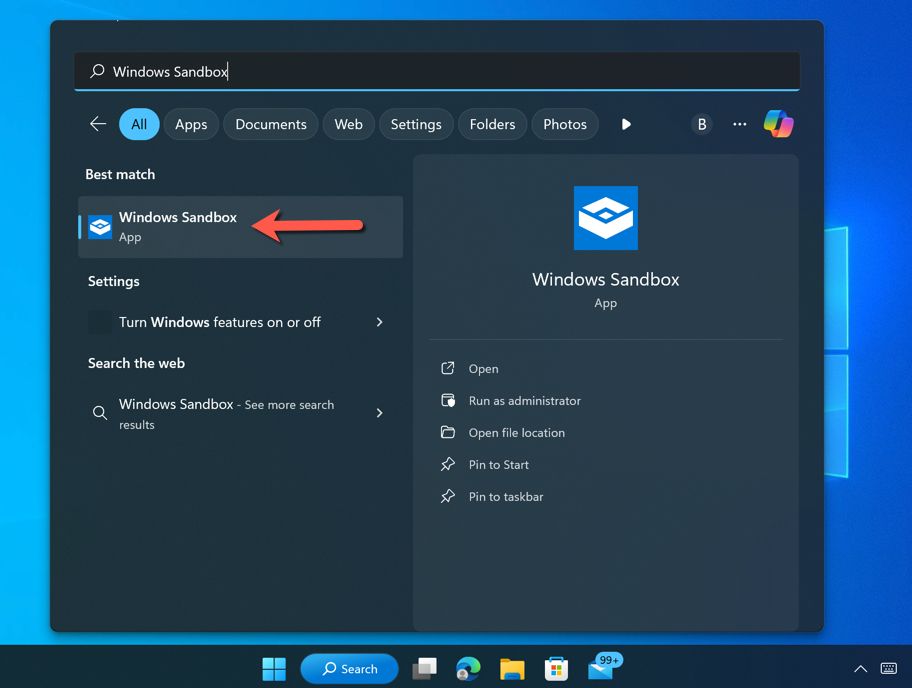
After the installation (and a quick restart), you can find “Windows Sandbox” in the Start menu, either manually or via a search.
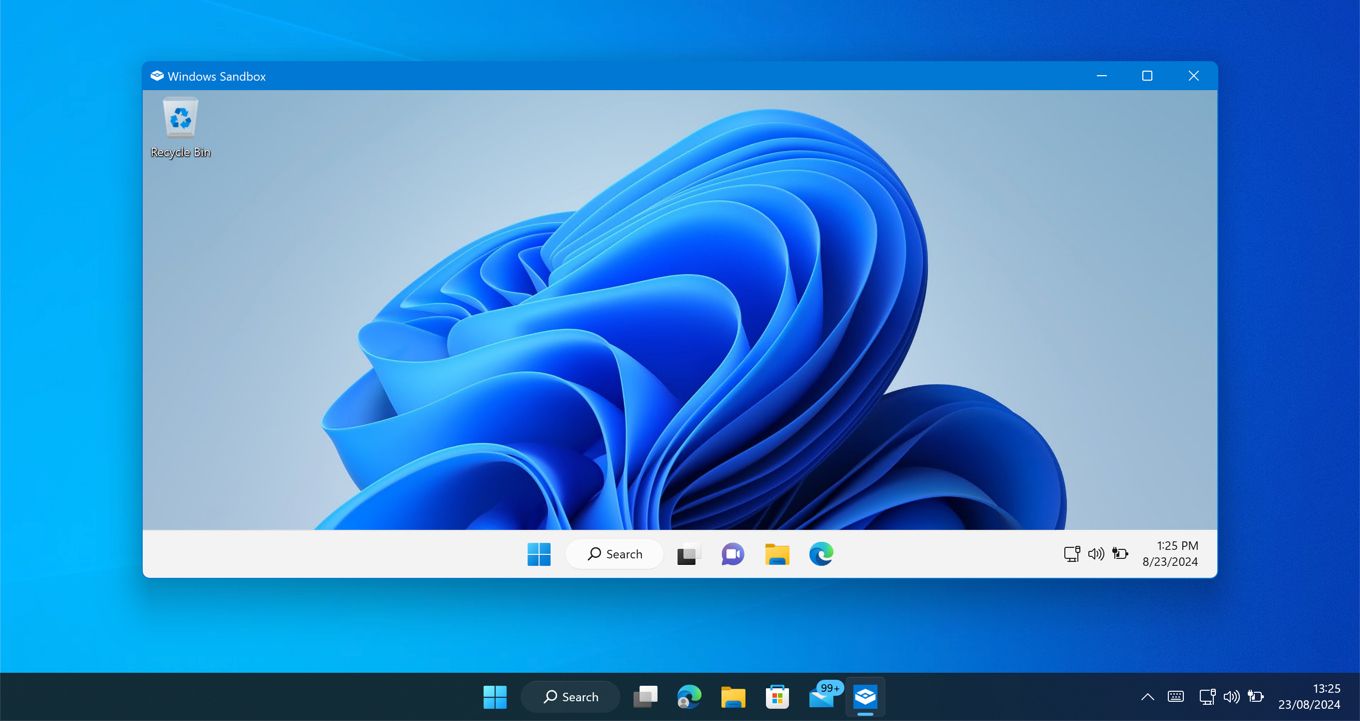
Once it opens, a replica of a clean Windows 10 or Windows 11 installation (depending on your own version of Windows) will appear for you to use.
Windows Sandbox Is Good Protection, But Remain Vigilant
The weak link in the chain is always going to be you (or whoever uses your PC). Windows Sandbox isn’t foolproof, and there are some attacks that the sandbox can’t protect you from if you don’t remain vigilant at first.
A good example is session hijacking. A rather famous incident in recent years was the attack on the Linus Tech Tips’ YouTube channel. An employee downloaded and opened a rogue PDF file, which contained rogue code. The code captured the session cookie for the channel from a web browser, allowing the attacker full access to the channel’s account as if they’d signed in themselves. No password required.
Mayhem ensued, but it didn’t have to be that way. For example, if that employee had opened the file in a fresh sandbox environment, then the attack would have failed. However, if the employee was signed in to the account in a web browser within the sandbox, the attack would still succeed.
The moral of the story? Use the sandbox as a sandbox for one thing at a time. If you want to test a file, you should only open that file. If you want to try out an app, only try that app, and don’t risk any of your personal information doing so.
Should you need to test both, just close the app, restart the sandbox, and try it in a fresh environment.
For Extra Sandbox Security, Block Network Access
There’s a way to beef up security in Sandbox to make it even more secure and prevent attacks (like the session hijacking I described above) from succeeding. If you block network access in Windows Sandbox, your sandbox can’t interact with any other device, whether it’s another local PC or a server hosted on the internet.
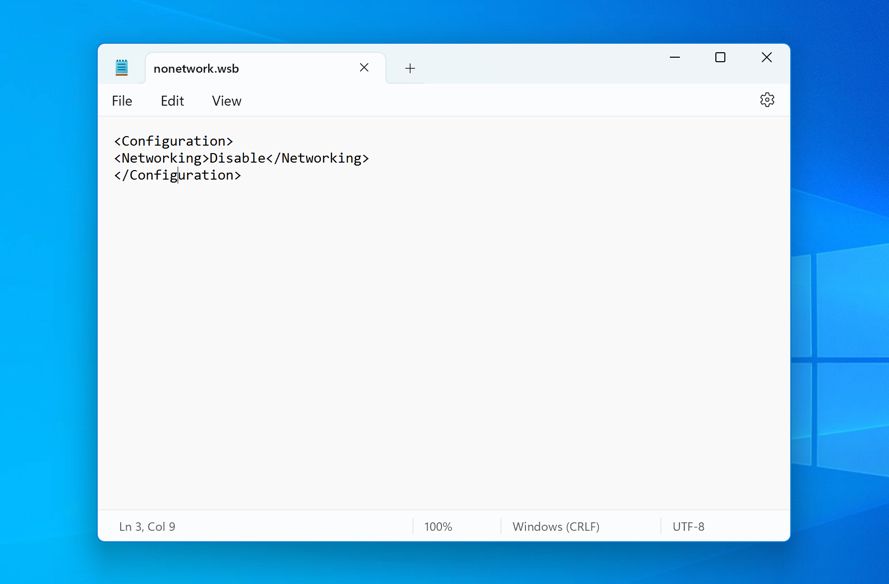
To do this, open Notepad and type in the following text:
<Configuration>
<Networking>DisableNetworking>
Configuration> Save the file with any file name you want using the “.wsb” file extension (e.g. nonetwork.wsb).
When you want to run your sandbox without network access, just double-click the file. It’ll run with that configuration, with access to your PC’s network adapter blocked entirely.
There are some other Windows Sandbox configuration settings you can add, too, including the ability to map a folder share or disable the virtual GPU. I usually run the sandbox with both the vGPU and networking disabled, just to make the sandbox more secure.
Can’t Use Windows Sandbox? Create a Custom Virtual Machine Instead
If you’re a Windows 10 or 11 Home user, you can’t use the sandbox, but you can use a virtual machine. It won’t be self-destructing, but the same principles can still apply. There’s no reason why you can’t keep a backup of a fresh virtual machine to revert to and give yourself a sandbox-style environment.
If you decide to run Windows 11 in a virtual machine, however, then the process is going to include setting up Windows in that environment. It won’t be as quick or seamless, and you may find that the impact on your system resources is greater.
I think Windows Sandbox is one of the best features in modern Windows, but it’s completely undersold and definitely underutilized. If you ever need to try out a risky app or file, don’t put your main system at risk. Just open up Windows Sandbox instead.
Source link